The Information Security Office recently held an informational Zoom meeting about best practices to secure university data. I wanted to share some of the key takeaways from the call. Use these tips to help keep your data safe.
First, let’s define the different data classification levels: public, sensitive, and confidential.
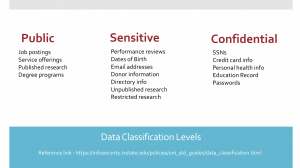
Public information includes any information that is meant for the wide public, which could include job postings, service offerings, published research, and more.
Sensitive information is any information that deemed sensitive like date of birth, email addresses, performance reviews, unpublished research, and more.
Confidential information includes social security numbers, credit card info, personal health info, education records, and passwords.
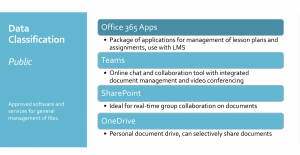
 Texas State University has specific tools available for handling each type of data classification. For data under the public classification, the appropriate tools to use include the Office 365 apps, Microsoft Teams, Sharepoint, and OneDrive.
Texas State University has specific tools available for handling each type of data classification. For data under the public classification, the appropriate tools to use include the Office 365 apps, Microsoft Teams, Sharepoint, and OneDrive.
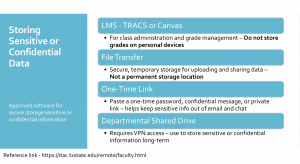
For sensitive or classified information the tools that are available are the approved learning management systems TRACS or Canvas, File Transfer, One-Time Link, and Departmental Shared drive.
Email Best Practices
The Information Security Office also shared best email practices including separating your work vs personal email, remove confidential information from emails, and not opening unknown links or attachments.

Also, refrain from using software that isn’t approved by the Information Security Office. Software is approved because Texas State can see how the data is being managed, but with unapproved software you are more vulnerable to have your data breached.
For more information on how to protect yourself online check out the Information Security Office webpage.
Cedrik Chavez is marketing and communications specialist student employee in the IT Marketing and Communications office.


